IceCTF
This ctf was going for about a month and it ended yesterday ! I performed good in this CTF with 1007 points 320'th position it was pretty easy ctf !
Yeah it's writeup-time and this page contains writeup of others through which i learnt something new ..
Ok this que was to find flag hidden somewhere in website i searched almost everywhere ...
apparently the solution was to use wget :(
wget -r -m 2 -l 10 "https://icec.tf" ('-r' recursive '-m' mirror -l level-depth )
grep -r "IceCTF{"
I too thought of that i was to lazzy
Ok this concept was completely new to me this question gave us hint about searching about domain
1) we have to do DNS record lookup using a tool called dig but by default it lookup in -A record (ipv4 address)
what we have to look is -TXT record (i don't even know it exists .. ) so here it goes ..
dig -t TXT search.icec.tf/ (-t for specifying type )
The question states that miners didn't have made any acounts and you still need flag !!
I was trying sqli 'admin limit 1 -- ' coz there was condition mysqli_num_rows($result) == 1 but ...
i didn't notice Database was empty !!! so i had to create one using ' UNION select 1,2,3 -- ' (no of coloums has to be guessed )
Think of select as pop in stack it puts value 1 2 3 to the empty database :)
Ok we were given a midi file and there was a writeup that discomforted me .. but i fonund a good and simple one !
Acording to that what u have to do is use ur hexeditor exract the text remove unwanted stuff that's it !! you get flag!
In this question we were given a binary file all u have to do is carved a zip file which was password protected .. untill this i reached but cracking pass was a
challenge to me but .. the guy used a diffrent dict called jhon.txt to crack and i don't know why even after using it i couldn't crack pass using fcrackzip but if use
without -u (unzip) option i could get a possible pass list which had the correct pass too.. i am still working on it ...
I have no idea about this Writeup state's it is vulnerable to NoSqli which occurs in mondoDB and angularJs have to work on this later !!!
Yeahh this is my area but it's Heap Overflow Use After Free need to study
I didin't try this problem so i will come back after trying !!!
It is A cgi shellshock vulnerability no idea about it
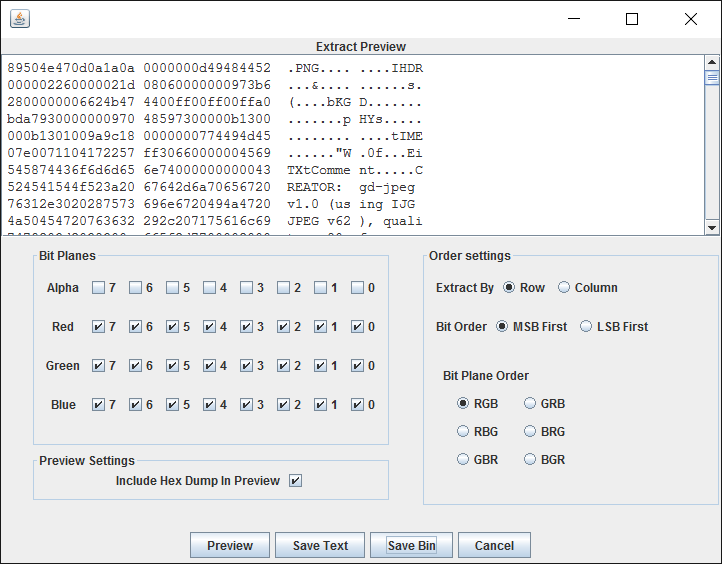
Ok this one is quite simpler than i thought i wrote py script to extrace ascii value in pixel but no use !!
But a PNG is embeded in the most signifiant bits of given image .. so to extract we have to use stegsolve -> Analyse -> DataExtract.
with all RGB options enabled and MSB first enabled and save it as png .. then open the png tada.. flag

I just did tcp.stream eq 1 to extract encode.pyc file and the use decompiler like unpyc3 after decompiling reverse the algorithim to decrypt the message !!
I found out there is XSS vulnerability and tried getting admin cookie .. but i didn't do one damm thing there was button which reports that to admin i didn't even see
so moral here is to inspect the source code properly !! but this does not stop here after u become admin u have a upload page now if u upload other than img it doesn't accepts
it's using file command to check that now do command injection file name : apple;cat flag* that's it ...